

Indian Journal of Science and Technology
DOI: 10.17485/IJST/v15i13.2102
Year: 2022, Volume: 15, Issue: 13, Pages: 592-602
Original Article
Vinod Desai1*, H A Dinesh2,3
1Assistant Professor, Department of Computer Science and Engineering, Angadi Institute of Technology and Management, Belagavi, 590009, Karnataka, India
2Professor and HOD, Department of Computer Science and Engineering, Nagarjuna College of Engineering and Technology, Bangalore
3Founder and Director, Cybersena (R&D) India Private Limited, Shreenagar, Belagavi, 590016
*Corresponding Author
Email: [email protected]
Received Date:12 November 2021, Accepted Date:23 February 2022, Published Date:29 March 2022
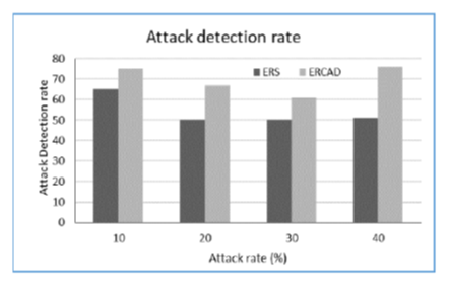
Objective: To reduce the cyber-attacks in IoT devices and also to provide security and reliable communication among the IoT devices and Edge servers, we have designed an Efficient Reputation-based Cyber-Attack Detection (ERCAD) mechanism for the Bigdata environment. Methods: This work presents an Efficient Reputation-based Cyber-Attack Detection (ERCAD) mechanism using the trust-based method. This work provides reliability and security by employing a trust-based security model and a feedback-based model. Moreover, to increase the network performance of the model which the existing system lacks, our model provides a reputation metric that classifies the malicious IoT nodes. Also, our model provides an efficient reputation cyber-attack detection communication metric for Bigdata Environment. Findings: Most of the Existing Reputation-Based Security (ERS)(1),(2),(3) models have achieved a good detection rate but have an increased failure rate. Furthermore, the ERS models have more throughput with more energy consumption and are less reliable and have not provided any QoS requirement and proper security for their models. Hence, the ERCAD model achieves a very good attack detection rate of 22.04% with a minimum detection failure rate of 33.89% for a wide range of attacks in comparison with Existing Reputation-Based Security (ERS) models. Moreover, the ERCAD improves throughput by 22.40% and with a reduction of energy consumption of 40.032% in comparison with Existing Reputation-Based Security (ERS) models and also is highly reliable by assuring QoS and security together. Novelty: The ERS models have failed to attain a better attack detection rate when the device is in the dynamic behavior. Further, are not efficient in modeling feedback reliability. Hence, our ERCAD model provides a better attack detection rate when the device is in dynamic behavior and also provides a security framework for classifying the malicious IoT nodes.
Keywords: Reliability; Security; Detection; BigData Environment; QoS requirement
© 2022 Desai & Dinesh. This is an open-access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited.
Published By Indian Society for Education and Environment (iSee)
Subscribe now for latest articles and news.