

Indian Journal of Science and Technology
Year: 2021, Volume: 14, Issue: 1, Pages: 76-85
Original Article
Alok Kumar Pani1*, Manohar M1, Rajdeep Kumar2
1Department of Computer Science and Engineering, CHRIST (Deemed to be University), Bangalore, India
2Employee, Banking Industry
*Corresponding Author
Email: [email protected]
Received Date:13 November 2021, Accepted Date:26 December 2021, Published Date:13 January 2021
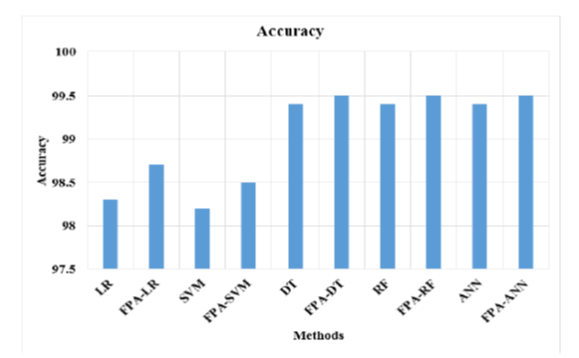
Background/Objectives Internet of Things (IoT) is an emerging technology that involves in monitoring the environment and the IoT networks are most vulnerable to attacks due to various number of devices connected in the network. The Intrusion detection technique has been applied to analyze the anomaly in the network. The Existing models have the limitation of inefficiency in the intrusion detection due to the overfit in the models. Methods/Statisticalanalysis: In this research, the Flower Pollination Algorithm (FPA) has been applied in the intrusion detection method to increase the efficiency of the IoT network. The FPA method has the advantage of long distance pollination and flower consistency to analyze the features effectively. The FPA selects the features in the IoT network and apply the features for the classifier to detect the attacks. The classifiers such as Logistic Regression (LR), Support Vector Machine (SVM), Decision Tree (DT), Random Forest (RF) and Artificial Neural Network (ANN) are used to detect the intrusions in the network. Findings: This experimental result shows that the proposed FPA method with ANN has the accuracy of 99.5 % in detection and existing ANN has 99.4 % accuracy in detection. Novelty/Applications: The FPA method has the advantages of long distance pollination and flower consistency which helps to analyze the network features effectively.
Keywords: Artificial neural network; flower pollination algorithm; internet of things; intrusion detection; long distance pollination
© 2021 Pani et al.This is an open access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited. Published By Indian Society for Education and Environment (iSee)
Subscribe now for latest articles and news.