

Indian Journal of Science and Technology
Year: 2020, Volume: 13, Issue: 25, Pages: 2529-2536
Original Article
Dr. Charu Virmani1*,Neha Kaushik1, Mohak 1, Vishnu Mathur1, Sanskar Saxena1
1Manav Rachna International Institute of Research and Studies, Faridabad, 121004, Haryana, India
*Corresponding author
Email: [email protected]
Received Date:11 May 2020, Accepted Date:10 June 2020, Published Date:17 July 2020
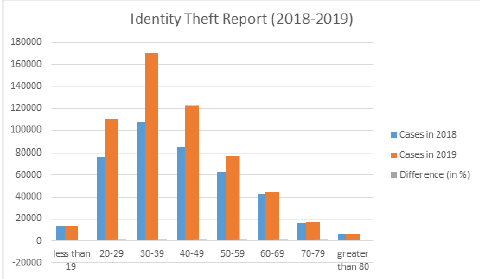
Objectives: To analyse the cybersecurity risks and their impact on the organizations. Researcher attempts to list down the issues and mitigation of Identity theft as a risk. Methods: This study develops a theoretical framework for future researchers and organizations for awareness and impact of Identity theft in area of cybercrime. The study has dogged various mechanisms by which watermarking can be applied to overcome to prevent identity theft attack. Findings: Researcher has emphasized the need for security solution and listed the steps to achieve security. An integrated view of identity theft and watermarking is formulated and proposed. The right balance between the application and techniques of watermarking opted will protect the user against the various types of identity theft attacks. Applications: Identity Theft has gained momentum in online space. The study highlighted various issues, consequences and economy of identity theft attacks with securing networks for unauthorized access. Watermarking plays an important role in authentication and authorization of data and proved a viable solution to mitigate identity theft attack.
Keywords: Cyberspace; identity theft; Security intelligence; watermarking
© 2020 Virmani,Kaushik, , Mathur, Saxena.This is an open-access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited. Published By Indian Society for Education and Environment (iSee)
Subscribe now for latest articles and news.