

Indian Journal of Science and Technology
Year: 2023, Volume: 16, Issue: 5, Pages: 357-366
Original Article
D R Somwanshi1*, Vikas T Humbe2
1Assistant Professor, Department of Computer Science, College of Computer Science and Information Technology (COCSIT), Latur, Maharashtra, India
2Associate Professor, School of Technology, Swami Ramanand Teerth Marathwada University Nanded, Sub-Center, Latur, Maharashtra, India
*Corresponding Author
Email: [email protected]
Received Date:16 October 2022, Accepted Date:08 January 2023, Published Date:07 February 2023
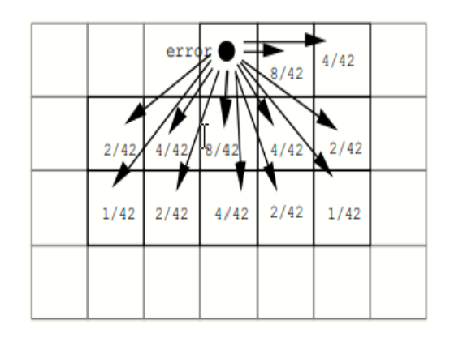
Objectives: Currently used visual-cryptography methods which use binary and gray-level images have some shortcomings such as large pixel expansion, poor visual quality of the reconstructed image, etc. Further modifications in visualcryptography methods are required to provide error-free and better results. It has been observed that the use of color images is more convenient and accurate in approach. Method: This research study presents a new and optimal scheme for the visual-cryptography which is centered on RGB color images. Jarvis halftoning is applied on each decomposed color channel that is used in share generation. A special code matrix is defined for the generation of color shares and the optimal reconstruction of the original image. The method is tested with color images of different sizes, no specific dataset is required. Pixel Expansion, The Aspect Ratio, and Contrast of the method is compared with the existing method, and found more enhanced result. Findings: The scheme projected eliminates the problems of large pixel expansion and poor visual quality in the reconstructed images. The performance of the method is tested with the different statistical measures and values obtained as Mean Square Error (MSE):0, Peak- Signal-to-Noise-Ratio (PSNR): ¥, Universal Index Quality (UIQ):1, etc. This means that the original image is completely recovered with good contrast. Novelty: Color images of varied sizes and channels can be processed by applying the Jarvis half-toning technique through the codebook calculated to abolish the problems of pixel expansion and to improve the superiority of the renovated image.
Keywords: Color HalfTone Images; Error Diffusion; Optimal Contrast; Secret and Secure Sharing Scheme; Expansion of Pixels
© 2023 Somwanshi & Humbe. This is an open-access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited. Published By Indian Society for Education and Environment (iSee)
Subscribe now for latest articles and news.