

Indian Journal of Science and Technology
Year: 2022, Volume: 15, Issue: 33, Pages: 1613-1623
Original Article
M Venkata Krishna Reddy1,2*, P V S Srinivas3, M Chandra Mohan4
1Research Scholar, Department of Computer Science and Engineering, Jawaharlal Nehru Technological University, Hyderabad, Telangana, 500075, India
2Assistant Professor, Department of CSE, Chaitanya Bharathi Institute of Technology(A), Hyderabad, Telangana, 500075, India
3Professor, Department of Computer Science and Engineering, Vignana Bharathi Institute of Technology(A), Hyderabad, Telangana, 500075, India
4Professor, Department of Computer Science and Engineering, Jawaharlal Nehru Technological University, Hyderabad, Telangana, 500075, India
*Corresponding Author
Email: [email protected]
Received Date:22 March 2022, Accepted Date:04 August 2022, Published Date:26 August 2022
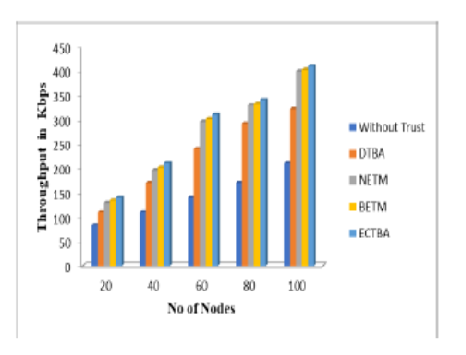
Objectives: To find an efficient security routing model based on trust adaptability by considering various transmission parameters that influence the node’s behavior. Methods: Enhanced Collaborative Trust Based Approach (ECTBA) was applied to isolate the malicious nodes from routing by computing their enhanced collaborative trust value based on the node’s behavior using transmission parameters. Parameters that influence the node’s behavior like the number of data packets and control packets forwarded, dropped, or misrouted by the node are quantified to compute direct trust value and neighbor reputation. Node’s Enhanced Collaborative trust value was generated by the combination of direct and neighbor observations. Findings: The proposed strategy is compared with several cases like the Direct Trust Based Approach (DTBA), where routing involves trustworthy nodes categorized based on only direct trust, existing methods like Belief-dependent trust evolution method(BETM), Novel extended trust-dependent method (NETM) where routing is done with nodes that are categorized as trustworthy depending on direct and indirect observations and simple AODV routing performed with all the possible random nodes without any trust detection. The performance parameters of the proposed ECTBA exhibit a success rate of 10.2% in false positives detection (FPD),network throughput of 438.12 Kbps,and packet delivery ratio (PDR) of 92.3%.This method proves to be a better method when compared with the traditional trust-based security methods(BETM and NETM) in terms of efficiency. Novelty: This research suggested a novel and fine-tuned method for quantifying a node’s trustworthiness and for secure routing that coupled the direct and indirect observations into enhanced collaborative trustbased on the node’s behavior by considering the transmission parameters. The present work highlights the combination of data packets forwarding behavior and control packets forwarding behavior in computing enhanced collaborative trust to decide the involvement of intermediate trustworthy nodes’ which is not tried before but this study does.
Keywords: Dynamic Topology; Direct Trust; Neighbor Trust; Secure Routing; Enhanced Collaborative Trust
© 2022 Reddy et al. This is an open-access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited.
Published By Indian Society for Education and Environment (iSee)
Subscribe now for latest articles and news.