

Indian Journal of Science and Technology
DOI: 10.17485/IJST/v13i30.1152
Year: 2020, Volume: 13, Issue: 30, Pages: 3059-3069
Original Article
J Ramkumar1*, R Vadivel2
1Assistant Professor, Department of Computer Science, VLB Janakiammal College of Arts and Science, Kovaipudur, Coimbatore, 641042, Tamil Nadu, India
2Assistant Professor, Department of Information Technology, Bharathiar University,Coimbatore, 641046, Tamil Nadu, India
*Corresponding Author
Email: [email protected]
Received Date:14 July 2020, Accepted Date:30 July 2020, Published Date:19 August 2020
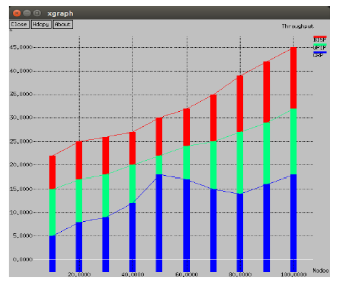
Background: Enhancing security and minimizing the delay is a significant task present in all modern networks. Dynamic emerging problems like node failure, route failure, intrusions, and security attacks lead the network to failure. Hence, there exist needs for development of a protocol that detects the intrusions and find the better route to destination. Objectives: The main objectives of this research is to understand the issues and challenges in routing that rise dynamically in cognitive radio ad hoc network and propose a bio-inspired routing protocol to enhance security and routing efficiency which will result in reduced delay cum energy consumption. Methods: This study proposes Bee Inspired Secured Protocol (BISP) for routing in cognitive radio ad hoc networks that focuses on increasing the security before sending data packets and decreasing the overall delay. An instinctive characteristic of Bees towards searching for food is utilized to design the proposed routing protocol, which selects the better path to the destination. To enrich the security during data transmission, Rivest Shamir Adelman algorithm is applied. The proposed protocol analyzes the security level of the route and neighbor node energy level before sending the data. Findings: NS2.35 simulator used to evaluate the performance of BISP. Simulation results indicate that BISP has better performance than the existing protocol (i.e., WPIP and GRP) in terms of throughput, packet delivery ratio, reduced delay and enhanced security. Novelty : Comprehensive analysis indicates that BISP have superior performance in classifying the intruding nodes, enhancing the security of data getting transmitted, and reducing the delay.
Keywords: Routing; security; intrusion; Bee; CRAHN
© 2020 Ramkumar & Vadivel.This is an open-access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited. Published By Indian Society for Education and Environment (iSee).
Subscribe now for latest articles and news.