

Indian Journal of Science and Technology
Year: 2023, Volume: 16, Issue: 23, Pages: 1733-1744
Original Article
P L Chithra1*, R Aparna2
1Professor, Department of Computer Science, University of Madras, India
2Research Scholar UNOM, Assistant Professor, Department of Information Technology, M.O.P. Vaishnav College for Women, India
*Corresponding Author
Email: [email protected]
Received Date:29 April 2023, Accepted Date:24 May 2023, Published Date:13 June 2023
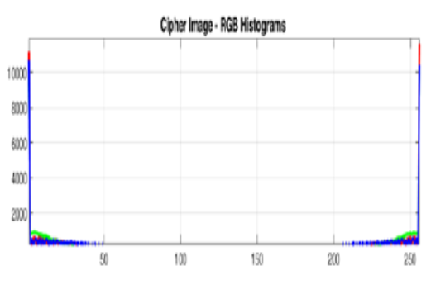
Objectives: Recent trend depicts a steep hike in the value of data. Data in all forms are vulnerable and especially multimedia data are fascinated by hackers Hence, strong security measure has to be applied before attempting to use the unsecure transmission medium for sharing secret / personal data. Methods: Dual Level Security Scheme (DLSS) is proposed which combines cryptography and steganography techniques to ensure double level security. Cipher image is obtained by applying Spiral Mapping and discrete cosine transformations (DCT) in RGB Layers. Then, the cipher image is hidden in the audio signal. Findings: SNR value is considered for normalizing the signals before embedding it, to obtain final signal without any traces of the hidden secret signal. Core objective of using DLSS is maintaining the secrecy when data transmission is taking place in any unsafe medium. Simulation results of our proposed method exhibit an average of 10% improvement and hence, DLSS outperforms well over the existing methods. Competence of the method is evident from the performed histogram analysis. Standard image dataset is used and directional correlation, PSNR, SSIM, and MSE are the considered measures to prove DLSS efficiency. Novelty: Here, a novel method Dual Level Security Scheme (DLSS) with spiral mapping is proposed to incorporate the aids of cryptography and steganography for enhanced efficiency.
Keywords: Cryptography; Steganography; RGB Layer Extraction; DCT; Spiral Mapping
© 2023 Chithra & Aparna. This is an open-access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited. Published By Indian Society for Education and Environment (iSee)
Subscribe now for latest articles and news.