

Indian Journal of Science and Technology
DOI: 10.17485/IJST/v15i17.2413
Year: 2022, Volume: 15, Issue: 17, Pages: 798-805
Original Article
M B Rajashekar1*, S Meenakshi Sundaram1
1Department of Computer Science & Engineering, GSSS Institute of Engineering & Technology for Women, Affiliated to VTU, Belagavi, Karnataka, India
*Corresponding Author
Email: [email protected]
Received Date:28 December 2021, Accepted Date:19 March 2022, Published Date:10 May 2022
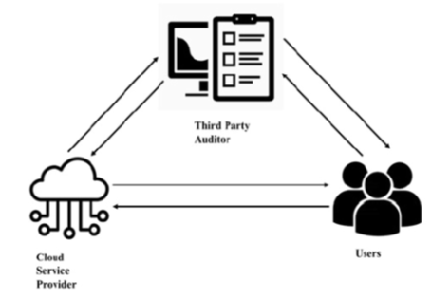
Background: To reduce the burden of the users to perform cloud audits. The tree based key handling method provides the structure format of data and increases performance in the search process. Methods: The Dynamic Attribute Tree method is proposed for Third-Party auditing to encrypt the data based on its attribute. The attributes are stored in tree structure along with data and key that helps to effectively improve the dynamic update of the data in the cloud. Findings: The proposed Dynamic Attribute Tree method has 6.7milliseconds computation time for 100 blocks of data and the existing Merkel Tree method has 7.5milliseconds computation time. Novelty: The Novelty of the project is the Dynamic Attribute Tree method uses bilinear mapping to verify the integrity of the data without retrieving the actual data from the cloud.
Keywords: Bilinear Mapping; Cloud audit; Cloud storage services; Dynamic Attribute Tree; and Third Party Auditing
© 2022 Rajashekar & Sundaram. This is an open-access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited.
Published By Indian Society for Education and Environment (iSee)
Subscribe now for latest articles and news.