

Indian Journal of Science and Technology
Year: 2023, Volume: 16, Issue: 4, Pages: 292-298
Original Article
Ekta Narwal1*, Ritu 1, Niram1, Deepika2
1Department of Mathematics, M.D. University, Rohtak, India
2Universitat Rovira I Virgili, Avinguda Catalunya, Tarragona
Received Date:11 October 2022, Accepted Date:22 December 2022, Published Date:03 February 2023
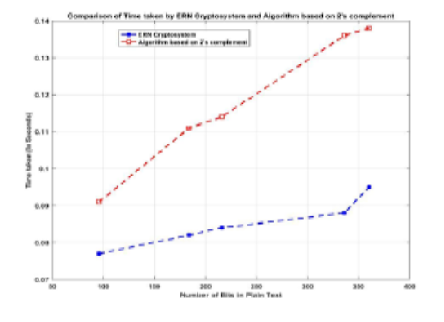
Objectives: To develop an algorithm based on classical encryption techniques that cannot be cryptanalyzed easily. Methods: We have proposed a new hybrid approach for the encryption and decryption of data. In this technique, some bits from the plain text, after converting it into binary form, are deleted and permuted in another place and placed back in the text. Findings: We examine the encryption and decryption times of various plaintexts of different sizes. Here, we compare the proposed ERN (Ekta Ritu and Niram) Cryptosystem with the algorithm based on 2’s complement method based on time complexity and efficiency. Novelty: A table displaying the encryption and decryption times of several input files of various sizes for the proposed algorithm and the already existing algorithm is given, with a relevant graph, proves the novelty of the cryptosystem. The experimental results show that the ERN cryptosystem has better performance and efficiency than the algorithm based on 2’s complement method. Keywords: Cryptography; Data Security; Substitution; Transposition; Cipher Text
© 2023 Narwal et al. This is an open-access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited. Published By Indian Society for Education and Environment (iSee)
Subscribe now for latest articles and news.