

Indian Journal of Science and Technology
Year: 2021, Volume: 14, Issue: 20, Pages: 1622-1634
Original Article
Jaspreet Kaur 1,* , Rajneesh Talwar 2 , Ashok Kumar Goel 3
Received Date:08 April 2021, Accepted Date:07 May 2021, Published Date:04 June 2021
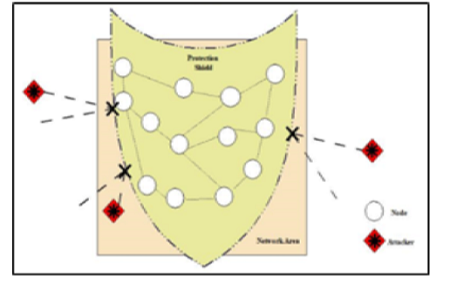
Background/Objectives: To mitigate network from amalgam attacks, this study is focussed on designing an efficient approach that can prevent the networks from intruders and secure the communication. Methods: A crossbreed approach, named ‘MOpt Shield,’ is proposed in this study. This proposed protocol utilizes the efficacy of the existing Cuckoo Search and Firefly Optimization Algorithm on basic AODV protocol along with the promising factors of the Intrusion Detection System. The proposed protocol is simulated using an NS-2 simulator with two different simulation scenarios, and PDR, Throughput, PLR, and Delay parameters are considered performance measures for the same. Findings: The proposed protocol finds the best selected nodes for communication and prepare separate list for the doubted nodes which further analyzed for attacker or non-attacker nodes. This will help to identify the best path with high energy and other capabilities for the efficient transmission of data. The performance of this proposed protocol is analyzed under 5 attacker nodes in which 2 are blackhole and 3 are DoS attacker nodes. For simulation, the scenario includes minimum 5 connections and maximum 25 connections between the 50 nodes with CBR traffic and 20m/s speed. The evaluated results show the astounding performance of the proposed protocol over the other existed protocols in terms of PDR, Throughput and Delay, and hence it reveals its capabilities. Novelty/Applications: The proposed protocol effectively handles the amalgam attacks and its novelty lie in its features of hybrid optimization and intrusion detection approach to find the route of transmission and the trusty nodes.
Keywords
MOpt Shield, Crossbreed, Cuckoo Search, Firefly Algorithm, Amalgam Attacks, Blackhole, DDoS, NS2 simulator
© 2021 Kaur et al. This is an open-access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited. Published By Indian Society for Education and Environment (iSee)
Subscribe now for latest articles and news.