

Indian Journal of Science and Technology
DOI: 10.17485/IJST/v16i37.1453
Year: 2023, Volume: 16, Issue: 37, Pages: 3148-3158
Original Article
Vipin Saxena1*, Pawan Kumar1
1Department of Computer Science, Babasaheb Bhimrao Ambedkar University, Lucknow, 226025, Uttar Pradesh, India
*Corresponding Author
Email: [email protected]
Received Date:14 June 2023, Accepted Date:30 August 2023, Published Date:09 October 2023
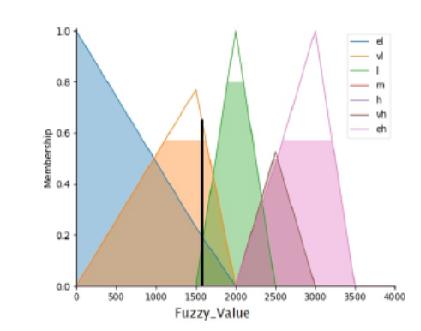
Objective: Internet technology is growing at a very fast rate around the globe and many of the countries are performing currency transaction through online mode. Due to increment of transaction of currency in an exponential manner, there is a need to include proper security features so that hackers or intruders could not hack the digital transaction carrying out between the two parties. Method: A new model using Unified Modeling Language (UML) is proposed which is developed in the hybrid mode with a combination of fuzzy rule-based computation, fingerprint authentication, Hash and Elgamal cryptography. The hybrid method is applied for secure transaction of the digital currency. The fuzzy rule based computation is used with Triangular Membership Function (TMF), which is based on current date and time. Fuzzy value creates a secret key and encrypts through Hash algorithm. Elgamal cryptosystem is used for encryption and decryption. The results obtained through hybrid method are tested through the concept of Finite State Machine (FSM) by generating the various test cases. Findings: The results obtained through hybrid method are tested through the concept of FSM by generating the various test cases. Novelty: In this work, mutual authentication as well as time stamp is also considered and the presented hybrid approach is based upon two-way authentication between client and user which is found to be very effective and may be used by the software industries for the customers especially related to the banking sectors.
Keywords: Fuzzy; Hash Algorithm; Cryptosystem; FSM; Test Cases and Validation
© 2023 Saxena & Kumar. This is an open-access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited. Published By Indian Society for Education and Environment (iSee)
Subscribe now for latest articles and news.