

Indian Journal of Science and Technology
DOI: 10.17485/IJST/v15i44.1387
Year: 2022, Volume: 15, Issue: 44, Pages: 2363-2374
Original Article
P Calduwel Newton1, F Jabez Samuel2*
1Department of Computer Science, Government Arts College (Affiliated to Bharathidasan University, Tiruchirappalli), Tiruchirappalli, 22, Tamil Nadu, India
2Department of Information Technology, Bishop Heber College (Autonomous) (Affiliated to Bharathidasan University, Tiruchirappalli), Tiruchirappalli, 17, Tamil Nadu, India
*Corresponding Author
Email: [email protected]
Received Date:04 July 2022, Accepted Date:16 October 2022, Published Date:30 November 2022
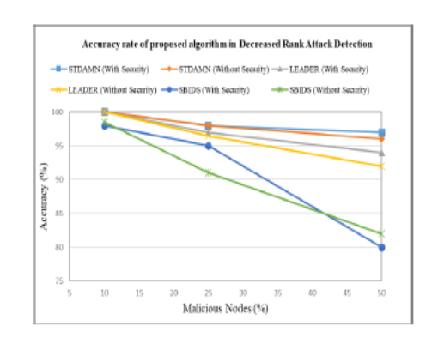
Objectives: To detect rank attacks during topology establishment and updated the RPL Destination Oriented Directed Acyclic Graph (DODAG) formation algorithm. The algorithm’s distributed module runs across all participating nodes, while the centralized module runs in the sink. Methods: The integrity and authenticity of control messages transmitted among two nodes and the sink are verified using a lightweight Hashed Message Authentication Code - Light-weight One-way Cryptographic Hash Algorithm (HMAC-LOCHA). The Secured Technique to Detect and Avoid Malicious Nodes (STDAMN) technique is proposed to overcome the rank attack of the nodes. Findings: The proposed scheme STDAMN outperforms the LEADER and SBIDS schemes when considering 50% malicious nodes, the accuracy rate of STDAMN is 3% higher than LEADER and 17% higher than SBIDS in Security mode whereas it is 4% and 14% higher in non-security mode respectively in the decreased rank attack. Again considering 50% malicious nodes, the accuracy rate of STDAMN is 2% higher than LEADER and 13% higher than SBIDS in with- Security mode whereas it is 2.2% and 16.1% higher in without-security mode respectively in the increased rank attack. Also indeed, the false positive rate for STDAMN is lower by 72.5% and 72%, 15.3% and 21.2% whereas the false negative rate for STDAMN is lower by 77.2% and 62.1%, 32.5%, and 39.5% on average for with-security and without-security respectively than LEADER and SBIDS in the decreased rank attack. Novelty: This paper presents a rank attack detection approach for non-storing mode RPL used in IoT to cope with both increased and decreased rank attacks to address this issue. The performance of the suggested technique is assessed both conceptually and through simulation using the Contiki-based Cooja simulator. The proposed technique surpasses state-of-the-art rank attack detection techniques in terms of detection accuracy and false positive/negative rate while maintaining acceptable network performance, according to simulation results.
Keywords: Security; RPL; Rank attack; HMAC; Malicious Node; DODAG
© 2022 Newton & Samuel. This is an open-access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited. Published By Indian Society for Education and Environment (iSee)
Subscribe now for latest articles and news.