

Indian Journal of Science and Technology
DOI: 10.17485/IJST/v15i46.1885
Year: 2022, Volume: 15, Issue: 46, Pages: 2548-2554
Original Article
A Sagaya Priya1*, S Britto Ramesh Kumar2
1Department of Computer Science, St. Joseph’s College (Autonomous), Affiliated to Bharathidasan University, Trichy, Tamil Nadu, India
2Department of Computer Science, St. Joseph’s College (Autonomous), Affiliated to Bharathidasan University, Trichy, Tamil Nadu, India
*Corresponding Author
Email: [email protected]
Received Date:17 September 2022, Accepted Date:04 November 2022, Published Date:14 December 2022
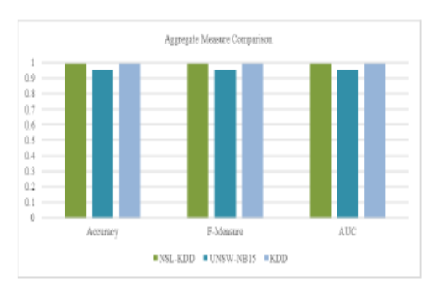
Objectives: To design an architecture that can effectively handle the imbalance levels and complexities in the network data to provide qualitative predictions. Methods: Experiments were performed with KDD CUP 99 dataset, NSL- KDD dataset and UNSW- NB15 dataset. Comparisons were performed with SAVAERDNN model. Oversampling technique is used for data balancing, and the stacking architecture handles the issue of overtraining introduced due to oversampling. Findings: The proposed Stacking and Feature engineeringbased Semi-supervised (SFS) model presents a combined architecture that integrates data balancing, feature engineering and a stacking-based prediction model that balances data to reduce imbalance, reduces the data size, and also provides highly effective predictions. Results: indicate 2% increase in accuracy levels on the UNSW-NB15 dataset and 10% increase in accuracy levels in the NSL-KDD dataset. Novelty: The architecture has been designed in a domainspecific manner. Multiple intrusion detection datasets, each with different levels of imbalance, have been used to depict the generic nature of the SFS model.
Keywords: Intrusion Detection; Data Imbalance; Stacking; Feature Engineering; Oversampling; Semi Supervised Learning
© 2022 Priya & Kumar. This is an open-access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited. Published By Indian Society for Education and Environment (iSee)
Subscribe now for latest articles and news.