

Indian Journal of Science and Technology
Year: 2023, Volume: 16, Issue: 16, Pages: 1205-1213
Original Article
Dhanashree K Toradmalle1*, K Amarendra2
1Associate Professor, Department of Computer Engineering, K J Somiaya Institute of Technology, Sion, Mumbai-77, Maharashtra, India
2Professor, Department of Computer Science and Engineering, Koneru Lakshmaiah Education Foundation, Vaddeswaram, 522502, Andhra Pradesh, India
*Corresponding Author
Email: [email protected]
Received Date:23 February 2023, Accepted Date:30 March 2023, Published Date:21 April 2023
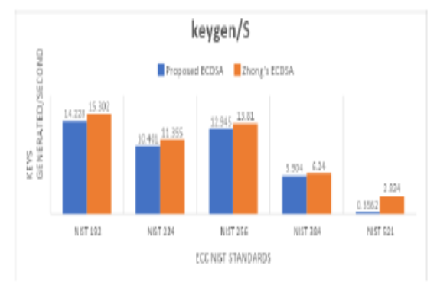
Objectives: To build a bridge to provide a solution by developing a lightweight ECDSA method that is not only lower in computational aspect but also is more secure than the Zhong’s ECDSA. Methods: The proposed research work performs cryptanalysis of Zhong’s ECDSA and demonstrates that the method fails to withstand MITM attacks. The proposed ECDSA uses only 1 elliptic curve point multiplication ECPM operation, 1 Modular multiplication operation and zero Modular Inverse operations making it lightweight in terms of computational time. Zero inverse operations save computational time as the process involves scalar mathematics which is time-consuming. Findings: Zhong’s ECDSA is not secure. Additionally, the technique takes 13.28% less time to sign data than the suggested ECDSA method. Through proofs, it is shown by comparison of the proposed ECDSA and Zhong’s ECDSA and cryptanalysis that the proposed ECDSA is more applicable in real time. Although Zhong’s Method for Signature verification at the Receiver end takes 8.2% more time, the recommended technique stands out in comparison to Zhong’s ECDSA w.r.t security. Novelty: The work is a detailed expression of the provablysecure attack-resistant light-weight digital signature based on elliptical curve for resource constrained applications. Advancing, the novelty of the work lies in the comparison of the two techniques w.r.t their performance parameters like number of keys generated, time taken to generate keys, number of keys verified, time taken for key verification, time taken for Signature generation and time taken for Signature verification.
Keywords: Digital signature; MITM; ECDSA; Replay attacks; Forgery attacks
© 2023 Toradmalle & Amarendra. This is an open-access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited. Published By Indian Society for Education and Environment (iSee)
Subscribe now for latest articles and news.