

Indian Journal of Science and Technology
DOI: 10.17485/IJST/v15i46.1658
Year: 2022, Volume: 15, Issue: 46, Pages: 2562-2569
Original Article
Owusu Nyarko Boateng1*, Boadu Nkrumah2, Victoria Boafo3, Akwasi Amponsah3, Lord Anertei Tetteh4, Justice Aning5, Kornyo Oliver1, Adebayo Felix Adekoya1, Isaac Kofi Nti6, Faiza Umar Bawah1, Nicodemus Awarayi Songose1, Boateng Samuel1, Patrick Kwabena Mensah1, Peter Nimbe1, Vivia Akoto Adjepong1, Ricardo Agbedanu7,Benjamin Asubam Weyori1
1The Department of Computer Science and Informatics, University of Energy and Natural Resources, Ghana
2The Department of Computer Science, Kwame Nkrumah University of Science and Technology, Ghana
3The Department of ICT & Mathematics, Mampong Technical College of Education, Ghana
4The Department of Computer Engineering, Koforidua Technical University, Ghana
5The Department of Computer Science, Sunyani Technical University, Ghana
6School of Information Technology, University of Cincinnati, Ohio, USA
7African Centre of Excellence in Internet of Things, University of Rwanda, Rwanda
*Corresponding Author
Email: [email protected]
Received Date:06 September 2021, Accepted Date:16 September 2022, Published Date:14 December 2022
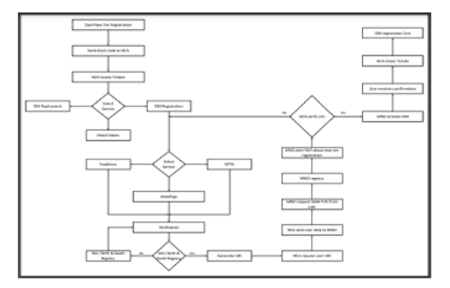
Background: Most subscriber identification module (SIM) which usually finds their way to mobile phone users are primarily unregistered or pre-registered. Criminals buy these SIM cards, which have fake personal information, activate them and then use them as a channel of attacking vulnerable mobile phone users. Objective: to investigate the existing standards of the registration process, the weakness and how fraudsters leverage the shortcomings of the existing registration to attack unsuspecting subscribers. Methods: The study also proposed an automated theoretical model as an augmented model to ensure the SIM registration process and implementation become secure. Results: In our investigation, we identified that there had been a rise in fraudulent activities in Ghana, and the criminals have adapted to the new trend of committing a crime using mobile phones. The research presented a proposed conceptual model and algorithm for the new SIM registration. The study further conducted a comparative analysis of the principal component adopted to measure the robustness of the registration platform. The criminals mostly use social engineering tactics to trick their victims into disclosing sensitive information or sending money for services yet to be rendered. MNOs request an ID card before registering and activating SIMs, yet criminals can outwit the registration processes and get SIM cards registered through unapproved channels. Conclusion: We found out that the robustness of our model shall prevent SIM pre-registration and unapproved SIM activation due to verification mechanisms in the proposed model. A cognitive learningsystem has automated the registration process that can identify multiple registrations and prevent unapproved activation.
Keywords: SIM Fraud; SIM card; Cognitive System; Mobile Network Operators; Intelligent decisionmaking; SIM Registration
© 2022 Boateng et al. This is an open-access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited. Published By Indian Society for Education and Environment (iSee)
Subscribe now for latest articles and news.