

Indian Journal of Science and Technology
Year: 2021, Volume: 14, Issue: 8, Pages: 725-737
Original Article
Kukatlapalli Pradeep Kumar1*, Vinay Jha Pillai2, K Sarath Chandra3, Cherukuri Ravindranath Chowdary4
1Assistant Professor, Computer Science and Engineering, School of Engineering and
Technology, Christ University, Bangalore, 560074, India. Tel.: +91 9686272678
2Electronics and Communication Engineering, School of Engineering and Technology, Christ
University, Bangalore, 560074, India
3Civil Engineering, School of Engineering and Technology, Christ University, Bangalore,
560074, India
4Associate Professor, Computer Science and Engineering, School of Engineering and
Technology, Christ University, Bangalore, 560074, India
*Corresponding Author
Tel: +91 9686272678
Email: [email protected]
Received Date:09 December 2020, Accepted Date:14 March 2021, Published Date:19 March 2021
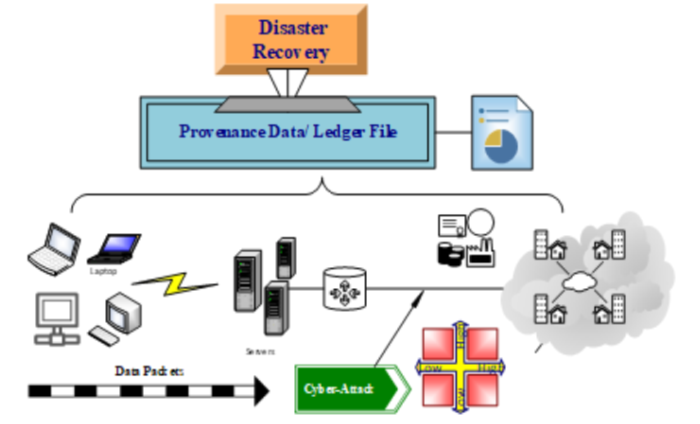
Objectives: To understand of data provenance applications towards cyber security for disaster recovery. To design an attack scenario with appropriate use cases using unified modeling language. To construct and analyze the data collected in the selected private computer network using appropriate graphical representation and comparing variables with null hypothesis. Methods: In the existing methods, presence of provenance data is not available with respect to network attack scenarios of risk management. Information security deals about disaster recovery in the form of business continuity planning, however nowhere it specifies about genesis data and its lineage. We propose a methodology for trouble shooting issues concerning over cyber physical systems in private networks. Findings: The process of resolving problems is linked with risk management for fairer and guaranteed continued communication as usual. Identity of the systems and users are considered random variables to understand the association between them. These random variables are picked from the provenance data maintained at the administrator login of a specific private network. This association analysis is unique and provides appropriate outcomes for good decision-making at the time of attack scenarios in risk management. Novelty: Simulations and their results are represented to show the correlation between risk management and data provenance in the cyber world. The uniqueness and novelty lies in design part of the problem statement with regards to provenance and disaster recovery for computer networks.
Keywords: Cyber security; data provenance; risk management; business continuity planning; information security
© 2021 Pradeep Kumar et al.This is an open access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited. Published By Indian Society for Education and Environment (iSee)
Subscribe now for latest articles and news.