

Indian Journal of Science and Technology
Year: 2021, Volume: 14, Issue: 41, Pages: 3107-3113
Original Article
G Amudha1*
1Associate Professor, Computer Science and Business Systems, R.M.D Engineering College, Chennai, 601206, India
*Corresponding Author
Email: [email protected]
Received Date:11 March 2021, Accepted Date:23 November 2021, Published Date:06 December 2021
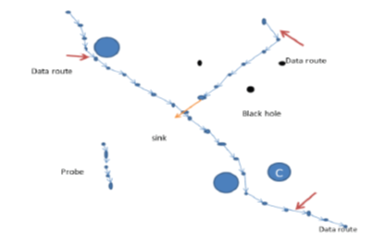
Objective: Main objective is to provide a secure router for transferring the valuable data being sensed. One of the major security threats in WSN is the Black hole attack, due to which incoming and outgoing traffic is silently discarded without informing the source that the data did not reach its intended recipient. Overcoming the Black hole attack in WSN is a current research topic. So, the proposed method of trust based secure routing will overcome the black hole attack. Method: The method implemented is integrated as Active Trust to the existing AODV routing protocol to avoid the Black hole attack in WSN. ActiveTrust can relevantly maintain the data route success quality and capacity against black hole attacks and can optimize network lifetime. Findings: Packet delivery ratio and Throughput are measured considering the attack and applying the method implemented. It is noticed that packet delivery ratio is less when there is an attack, and it gets increased when the attack is been rectified by Active trust method. Novelty: Trust based secure routing when compared with existing protocol AODV the attack is reduced and the throughput gets increased by reducing the packet loss. Our approach is efficient in terms of throughput and PDR. As trust factor is so important factor while compared to other factors like Node identity, Node Address etc., our proposed system is efficient. Because node identity can also be spoofed and node address can also be modified by an intruder, but the trust calculation based on the activity of the node cannot be modified by any attacker, because it involves the neighbour node to calculate the trust.
Keywords: Black hole attack; AODV; Trust; Secure routing
© 2021 Amudha. This is an open-access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited. Published By Indian Society for Education and Environment (iSee)
Subscribe now for latest articles and news.