

Indian Journal of Science and Technology
DOI: 10.17485/IJST/v14i38.1401
Year: 2021, Volume: 14, Issue: 38, Pages: 2934-2945
Original Article
Rajan Aswanandini1,2, Chandran Deepa3*
1Assistant Professor, Department of Computer Science, KG College of Arts and Science, Coimbatore, 641037
2Ph.D Scholar, Sri Ramakrishna College of Arts and Science, Coimbatore, 641006
3Associate Professor, Department of Information Technology, Coimbatore, 641006
*Corresponding Author
Email: [email protected]
Received Date:02 August 2021, Accepted Date:17 October 2021, Published Date:18 November 2021
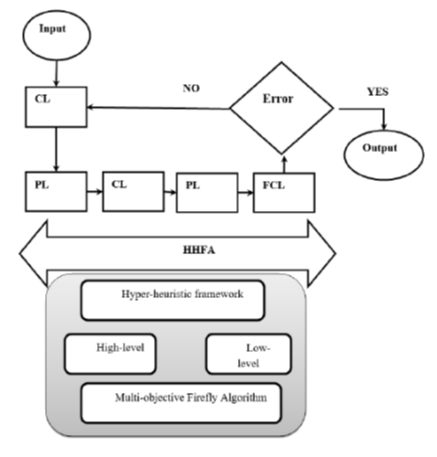
Objectives: A highly accurate Intrusion detection model is developed that classifies both the network-based and host-based intrusions without any complexity issues. Method: An optimized Deep Learning (DL) algorithm of IDS model is presented in the form of a Hyper-Heuristic Firefly Algorithm based Convolutional Neural Networks (HHFA-CNN). This proposed HHFACNN reduces false values and improves accuracy without increasing the complexities. Findings: The proposed HHFA-CNN system is performed on two network traffic datasets: NSL-KDD and ISCX-IDS. The outcomes demonstrated that the proposed HHFA-CNN model gives predominant execution than the other existing models. Novelty: The proposed model has employed a novel Hyper-Heuristic Firefly Algorithm for optimizing the hyper-parameters of the CNN. This model maintains the standard guidelines of the firefly algorithm and applies the high-level technique for controlling the exploration and determination of low-level heuristics.
Keywords: Big data; Cyber security; Intrusion detection system; Hyper-Heuristic Firefly Algorithm; Convolutional Neural Networks
© 2021 Aswanandini & Deepa. This is an open-access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited. Published By Indian Society for Education and Environment (iSee)
Subscribe now for latest articles and news.