

Indian Journal of Science and Technology
Year: 2023, Volume: 16, Issue: 9, Pages: 640-647
Original Article
Salunkhe Madhav Jagannath1, Rajendra B Mohite2, Mukesh Kumar Gupta3*, Onkar S Lamba4
1Research Scholar, Department of ECE, Suresh Gyan Vihar University, Jaipur, India
2Assistant Professor, Department of EXTC, Bharati Vidyapeeth College of Engineering Navi Mumbai, India
3Professor, Department of Electrical Engineering, Suresh Gyan Vihar University, Jaipur, India
4Professor, Department of ECE, Suresh Gyan Vihar University, Jaipur, India
*Corresponding Author
Email: [email protected]
Received Date:14 January 2023, Accepted Date:05 February 2023, Published Date:05 March 2023
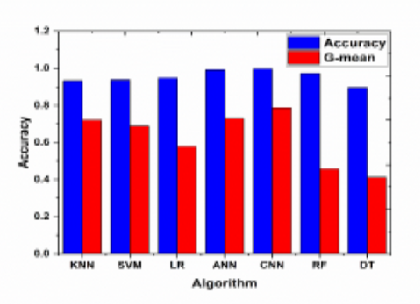
Objectives: To fix the security issues of devices in internet of things (IOT) systems that arise when Machine learning (ML) and Deep Learning algorithm (DLA) are implemented in the IOT systems. Methods: Each packet of IoT threats has been filtered by using suitable attack model for primary attack detection. In deep learning, network traffic field’s information is extracted from of packet and is used as the training features. Attack is proposed to be detected by the use of database-based features of attack. If attack is found then packet will be discarded along with update feedback to filtering stage for primary attack detection. Knowledge Discovery and Data Mining (KDD) dataset is used in this study. Different types of Mirai attack are considered for classification. The performance of the proposed method has been compared in terms of accuracy and execution time with earlier work using traditional ML-DL methods. Findings: The proposed technique is seen to achieve high accuracy level at the least computational time, concurrently with much higher recall and G-mean values Several algorithms are used to secure the IOT devices from various types of threats and a comparison is depicted with their accuracy and execution time. Results show that the proposed methodology using Convolution neural network (CNN) for classification, can achieve the accuracy ~0.9976 with execution time1.30 sec and G-mean 0.7865 only. Novelty: The proposed method is essentially a judiciously configured ML- DL technique which is novel and exhibits better performance in terms of mitigating IoT threats.
Keywords: IOT devices and threats; Machine Learning; Deep Learning; KDD; Security and privacy
© 2023 Jagannath et al. This is an open-access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited. Published By Indian Society for Education and Environment (iSee)
Subscribe now for latest articles and news.