

Indian Journal of Science and Technology
DOI: 10.17485/IJST/v16i17.2030
Year: 2023, Volume: 16, Issue: 17, Pages: 1268-1275
Original Article
P Arul1, N Shanmugapriya2*
1Research Supervisor, Assistant Professor, Department of Computer Science, Government Arts College (Affiliated to Bharathidasan University, Trichy-24), Tiruchirappalli, 621 211, India
2Assistant Professor, Department of Computer Science, Government Arts College (Affiliated to Bharathidasan University, Trichy-24), Tiruchirappalli, 620022, India
*Corresponding Author
Email: [email protected]
Received Date:15 October 2022, Accepted Date:26 March 2023, Published Date:02 May 2023
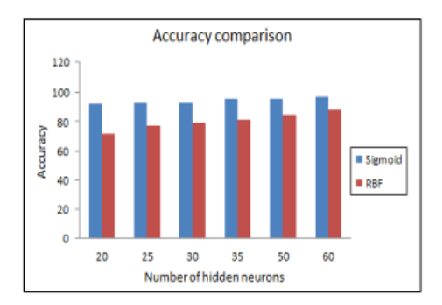
Objective: To develop a system based on fog computing to maintain the security of the user data and privacy in the IoT environment. The proposed work is intended to predict the assaults, automatically recognize known attacks, and select the appropriate defense mechanism to safeguard the private data in an IoT environment. Methods: The proposed approach is used to recognize a variety of intrusion methods, including DDOS, DOS, and multistage attacks developed by hackers with the explicit goal of seizing control of the entire IoT network and capturing the precious data. Initially the proposed work involves training the algorithm with a small amount of data, and when dynamic data begins to flow into IOT devices, the trained part will identify the potential attacks based on the earlier pattern built. Finding: The experimental evaluation is carried out for the proposed IDMAL along with two more existing algorithms ANN and Naïve Bayes to determine the performance of the proposed algorithm. The experimental results it is quite clear that the IDMAL after 12.3 seconds of training the attack detection accuracy is 97.1% with a false rate of 0.31%. Novelty: With a higher level of accuracy and precision, the suggested IDMAL algorithm makes use of cutting-edge methodologies to interpret attacks in advance utilizing a prediction mechanism from the IoT traffic data. The proposed algorithm is compared with two of the well-known existing algorithms namely ANN and Naïve Bayes and from the experimental result; it is quite obvious that the proposed algorithm is much more accurate and precise in detecting the attacks.
Keywords: Iot; Cloud computing; Fog computing; Security; Machine learning
© 2023 Arul & Shanmugapriya. This is an open-access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited. Published By Indian Society for Education and Environment (iSee)
Subscribe now for latest articles and news.