

Indian Journal of Science and Technology
DOI: 10.17485/IJST/v14i24.1708
Year: 2021, Volume: 14, Issue: 24, Pages: 2005-2033
Original Article
S Z Hussain1, Manoj Kumar1*
1Department of Computer Science, Jamia Millia Islamia, New Delhi, India
*Corresponding Author
Email: [email protected]
Received Date:03 January 2021, Accepted Date:02 June 2021, Published Date:13 July 2021
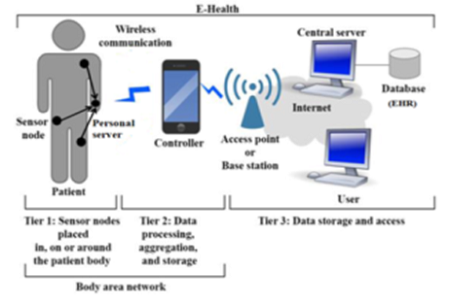
Objective: To review different key agreement schemes which are used to establish Wireless body area network (WBAN) on the basis of identified attacks and also evaluate the schemes on performance parameters. Method: In this paper, an overview of WBAN, its architecture, difference between WSN and WBAN, IEEE 802.15.6 specifications of WBAN, attacks in the environment and security essentials are discussed at first. It further divides the key agreement schemes into four classes and provides an extensive review of the schemes on the basis of distinct parameters viz. data confidentiality, node authentication, data integrity, mutual authentication, unforgeability, unlinkability, forward/backward secrecy, scalability, freshness, dos attack and node capture attack. Schemes are searched using the keywords- (“Traditional Key Agreement Scheme” OR “Physiological Key Agreement Scheme” OR “Signal Based Key Agreement Scheme” OR “Hybrid Key Agreement Scheme” OR “Security in Key Agreement Scheme”) AND (“Wireless Body Area Network” OR “WBAN” OR “Body Area Network” OR “BAN” OR “Body Sensor Network” OR “BSN” OR “Medical Body Area Network” OR “MBAN”). The papers are shortlisted around long stretches of 2003-2021 with a focus on recent work from IEEE Xplore, Springer, Science Direct, ACM, MDPI and Google Scholar databases. Schemes are analyzed against the mentioned attacks and the result of the comparative analysis is shown using tables and chart tools graphically. Findings: The wide coverage of the schemes in this review provides in-depth exposure to the shortcomings of the different schemes against the listed attacks which will provide a road map to the researchers to develop secure schemes in the future. Moreover, maximum schemes do not consider all the three aspects of performance viz. memory efficiency, computational efficiency and energy efficiency which are the foremost parameters in resource scarce environment of WBAN. Novelty: This review is unique as it analyzes the distinct key agreement schemes under specific attacks found in the literature while other review papers discuss the general aspects of the security threats and corresponding counter measures in WBAN environment. It also provides the performance analysis of the key management schemes which are missing from other review works.
Keywords: WBAN; IOT; Bio sensors; Security; Privacy; Attacks; Encryption; Key agreement schemes; IEEE 802.15.6
© 2021 Hussain & Kumar. This is an open-access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited. Published By Indian Society for Education and Environment (iSee)
Subscribe now for latest articles and news.