

Indian Journal of Science and Technology
Year: 2024, Volume: 17, Issue: 1, Pages: 1-15
Original Article
Kanthimathinathan Mangayarkkarasi1*
1Associate Professor, Department of Computer Science, D.G.G.A. College For Women, Mayiladuthurai, Tamil Nadu, India
*Corresponding Author
Email: [email protected]
Received Date:22 March 2023, Accepted Date:07 December 2023, Published Date:05 January 2024
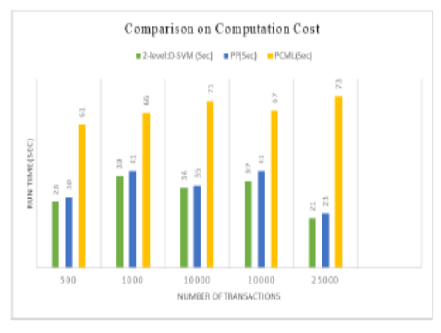
Background/ Objectives: It is becoming more common for data owners to outsource data mining tasks and storage to cloud service providers as a result of the rising costs of maintaining IT infrastructures for large-scale data mining. This trend, however, also raises security concerns about unauthorized breaches of data confidentiality and outcome integrity. Methods: This research considers this scenario in which cloud user can encrypt their data and store it to cloud environment. In order to perform mining operation, the user needs to outsource the task to cloud servers. Then, the cloud server performs the mining task on the encrypted data and share the encrypted association rule to the cloud user. Yet, existing single cloud server systems have privacy leakage issues since their work focuses on either database privacy or item privacy. To remedy this gap in the literature, this study maintains both database privacy and item privacy during the frequent itemset mining process. For item privacy, it first describes a universal safe multiplication protocol with a single cloud server. We build the inner product rules, comparison rules, frequent itemset protocol, and final association rule mining process that is secure against privacy leaking on top of this multiplication protocol. During this Association Rule Mining (ARM) operation, it provides two level of protection to data privacy. This model is designed with distributed Elgamal cryptosystem and sub-protocols for item and database privacy along with Deep learning-based Support Vector Machine (SVM) for secure rule generation. Findings: The proposed method is named as two-level privacy preserving method association with Deep SVM model (2-level:D-SVM), provides guaranteed solutions to the confidentiality of the outsourced cloud data and minimizes the user interaction during association rule mining task. Here, data on breast cancer and heart disease are used, and the effectiveness of the proposed model is demonstrated by comparison to existing models. According to the study, at 25000 transactions, the proposed 2-level:D-SVM model stands for 52% and 50% more efficient than Parallel Processing (PP) and Privacy-preserving Collaborative Model Learning (PCML) techniques in terms of computing cost. Additionally, the proposed model performs 34%, 22%, 6%, and 4% better in terms of execution time than the PP, Apriori, Eclat, and FP-growth techniques, respectively. Novelty: The proposed method is built on a set of well-constructed 2-level secure computation techniques that not only maintains confidentiality of data and query confidentiality, but additionally allows the data owner to operate offline throughout data mining. When compared with previous attempts, this technique provides a higher degree of privacy, in addition, lowers the computation cost for data owners.
Keywords: Association Rule mining, Cloud, Data mining as a service, Deep learning, SVM
© 2024 Mangayarkkarasi. This is an open-access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited. Published By Indian Society for Education and Environment (iSee)
Subscribe now for latest articles and news.