

Indian Journal of Science and Technology
Year: 2020, Volume: 13, Issue: 21, Pages: 2080-2093
Original Article
Ummer Iqbal Khan1∗, D.S. Oberoi1
1 National Institute of Electronics and Information Technology, Srinagar/Jammu, India
∗Corresponding author:
Ummer Iqbal Khan
National Institute of Electronics and Information Technology, Srinagar/Jammu, India
Email: [email protected]
Received Date:31 March 2020, Accepted Date:31 May 2020, Published Date:22 June 2020
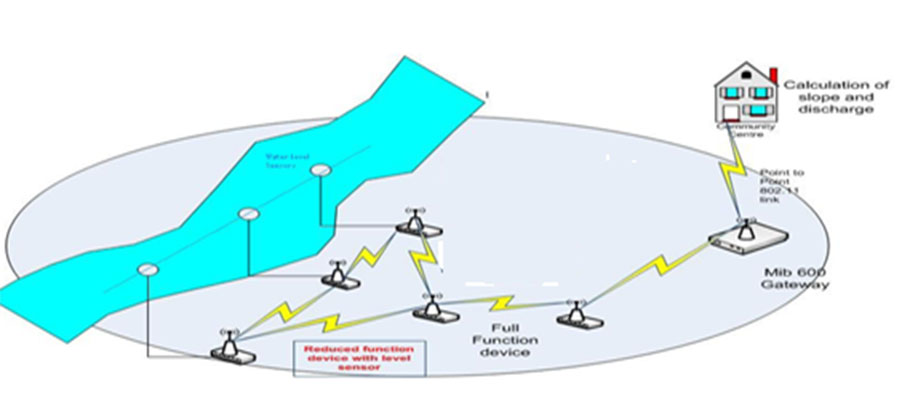
Objectives: To propose a design of an early flood warning system based on IOT with a strong emphasis on the security requirements of such systems. Methods/Analysis: The design of an early flood warning system is based on measuring the hydrological parameters of a river, which include water level and discharge through an IOT based network. To calculate the discharge of water in a river, Manning's equation has been employed. Security protocols based on elliptical curve cryptography has been proposed for authenticating the real-time hydrological data. The proposed security protocols have been formally validated and verified against various active and passive attacks using AVISPA and Scyther. Simulation of the proposed scheme has also been carried out on the TOSSIM simulator using the TinyECC library to estimate the radio and CPU energy overheads. Findings: The formal security validation of the proposed authentication scheme indicates that the scheme is SAFE against various active and passive attacks. The simulation on Scyther indicates that no attacks have been found in proposed authentication protocols. The AVISPA validation also declares the scheme as SAFE as all-important security goals have been achieved. The Energy analyses on TOSSIM indicate that each node in the scheme requires 133 mJ for radio transmission and 59 mJ for CPU operations about the Mica2 Energy Model. Novelty/Improvement: Researchers have proposed many designs and schemes for early flood warnings without giving much emphasis to the security of such systems. The paper focuses on the security requirements of such systems.
Keywords: IoT; flood warning; authentication; ECC; AVISPA; Scyther; TinyOS; TinyECC; TOSSIM
© 2020 Khan, Oberoi. This is an open-access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited.
Published By Indian Society for Education and Environment (iSee)
Subscribe now for latest articles and news.