

Indian Journal of Science and Technology
Year: 2023, Volume: 16, Issue: 2, Pages: 133-145
Original Article
V Rojasree1*, J Gnana Jayanthi2
1Research Scolar, Department of Computer Science, Rajah Serfoji Govt. College(A), (Affiliated to Bharathidasan University), Thanjavur, 613005, Tamil Nadu, India
2Assistant Professor, Department of Computer Science, Rajah Serfoji Govt. College(A), (Affiliated to Bharathidasan University), Thanjavur, 613005, Tamil Nadu, India
*Corresponding Author
Email: [email protected]
Received Date:22 September 2022, Accepted Date:18 December 2022, Published Date:16 January 2023
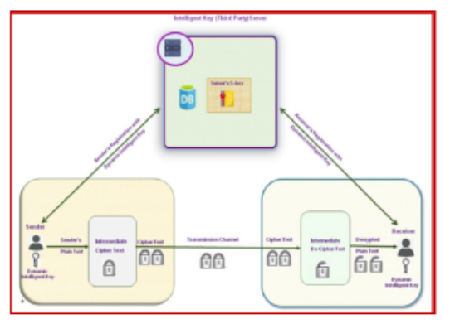
Objectives: To propose a new novel and unique cryptosystem with interfaces for the designed cryptosystem and to implement and test the new designed methodologies. Methods: The Tamil Unicode is used to convert the Plain text (Sender’s message) to Intelligent Key Cryptography system (IKC) Intermediary code. This intermediary code is converted to IKC cipher text by transpositioning characters with integer digit values of Time in positive direction. IKC decryption of cipher text (received message) to Intermediary code is done using Tamil Unicode and then this is converted to plain text by trans-positioning characters with integer digit values of Time in negative direction. The IKC algorithm developed thus address the discrepancies for the existing algorithms based on the literary survey done. Findings: In the proposed IKC algorithm, the key and key space are generated dynamically from the system Time and the system font Tamil Unicode; thus, reducing the key maintenance problems of the existing algorithms. In current cryptography algorithms, work is based on the assumption that the key value never comes to zero. But all the algorithms are mathematical calculations which will return to zero at an infinite point. This drawback is overcome in IKC algorithm by taking the Time the real infinity. The value of the time once passed will never return. The entire algorithm works in a secure shell developed using C++ and has proved to satisfy the needs of the objective of a robust cryptosystem. Comparative analysis shows that IKC works better compared to the existing system. Novelty: The IKC algorithm displays as: (i) keys are generated dynamically, (ii) cipher once formed is never repeated, even if the same plaintext is enciphered again, and (iii) it satisfies NIST policies.
Keywords: IKC Encryption; IKC Decryption; AIRKGS; Dynamic key; Postquantum cryptography
© 2023 Rojasree & Jayanthi. This is an open-access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited. Published By Indian Society for Education and Environment (iSee)
Subscribe now for latest articles and news.