

Indian Journal of Science and Technology
Year: 2024, Volume: 17, Issue: 10, Pages: 870-880
Original Article
Shwetambari Borade1*, Parshva Chetan Doshi2, Darsh Bhavesh Patel2
1Assistant Professor, Cyber Security, Shah & Anchor Kutchhi Engineering College, Mumbai, Maharashtra, India
2Student, Cyber Security, Shah & Anchor Kutchhi Engineering College, Mumbai, Maharashtra, India
*Corresponding Author
Email: [email protected]
Received Date:19 January 2024, Accepted Date:30 January 2024, Published Date:23 February 2024
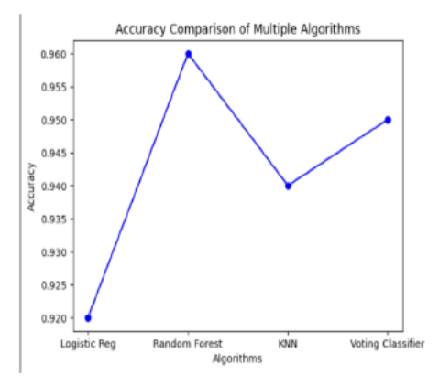
Objectives: To enhance cyber security by implementing advanced algorithms to swiftly identify and neutralize phishing threats. Also, to bolster user protection, fortify data integrity, and ensure a resilient defense against evolving cyber threats. Methods: MaliceSpotter aims in classifying user-entered URLs by analysing 28 features, using algorithms like Logistic Regression, Random Forest, and KNN, combined via a Voting Classifier. Dataset on Kaggle provides diverse samples for evaluation. This methodology's unique aspects include multiple algorithm integration and the utilization of Kaggle as a data source. Findings: MaliceSpotter demonstrates a commendable accuracy of 95%, effectively classifying input URLs as phishing or legitimate. The system's uniqueness lies in its provision of a detailed report on URL behavior, facilitating informed decision-making. The implementation of ensemble learning is notable, particularly the introduction of the Voting Classifier. This approach leverages various algorithms, successfully incorporating bagging and voting concepts. Through the Voting Classifier, MaliceSpotter gains insights into the working of machine learning algorithms, enhancing the scrutiny of URL behavior. This innovative feature sets MaliceSpotter apart, offering a nuanced perspective on the reliability of URLs through the collective input of diverse algorithms. Novelty: MaliceSpotter uniquely combines diverse algorithms, leveraging a voting classifier for robust results. Continuously updating in real time, it meticulously dissects URLs into 28 parts, ensuring thorough scrutiny and effective detection.
Keywords: Phishing, Machine Learning, Web Security, Voting Classifier, Bagging
© 2024 Borade et al. This is an open-access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited. Published By Indian Society for Education and Environment (iSee)
Subscribe now for latest articles and news.