

Indian Journal of Science and Technology
Year: 2024, Volume: 17, Issue: 13, Pages: 1323-1330
Original Article
V Elamurugu1*, D J Evanjaline2
1Research Scholar, Department of Computer Science, Rajah Serfoji Government College (Autonomous), Affiliated to Bharathidasan University, Tanjore, Tamil Nadu, India
2Assistant Professor, Department of Computer Science, Government Arts College, Affiliated to Bharathidasan University, Thiruverumbur, Trichy, Tamil Nadu, India
*Corresponding Author
Email: [email protected]
Received Date:06 January 2024, Accepted Date:29 January 2024, Published Date:22 March 2024
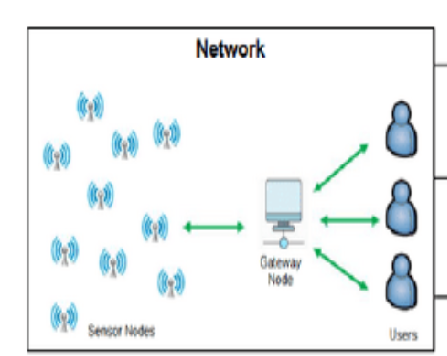
Objectives: The research aims to design an architecture for secure transmission of data in wireless sensor networks. Methods: The method involves three main pillars: authentication, data encryption, and dynamic routing. Extensive simulations have been conducted to evaluate the suggested method in terms of energy consumption, memory footprint, packet delivery ratio, end-to-end latency, execution time, encryption time, and decryption time. Findings: For authentication, a dynamic key is used to power an improved salt password hashing method. Data encryption is performed using format-preserving encryption (FPE) with the appended salt key. Dynamic routing is implemented using a cluster-based routing technique to enhance network efficiency in terms of power consumption and security. The execution time for MD5 ranges from 15 to 22 milliseconds, while for SHA-1 it ranges from 16 to 23 milliseconds and for the proposed salt key generation it is 1 to 5 milliseconds. Similarly, in terms of energy consumption, memory footprint, packet delivery ratio, end-to-end latency, execution time, encryption time, and decryption time the proposed method shows promising results in ensuring the integrity and security of transmitted encrypted data. Novelty: The presents a novel architecture with enhanced cluster head-based selection algorithm that combines dynamic key-based authentication and secure data routing to establish a safe environment for data transmission in wireless sensor networks. This research works offers a method for encrypting text with a dynamic salt key that is safe, energy-efficient, and lightweight.
Keywords: Wireless Sensor Network, Dynamic Key, Authentication, Hash function, Salt algorithm, Dynamic routing, Node clustering, Format-preserving encryption
© 2024 Elamurugu & Evanjaline. This is an open-access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited. Published By Indian Society for Education and Environment (iSee)
Subscribe now for latest articles and news.